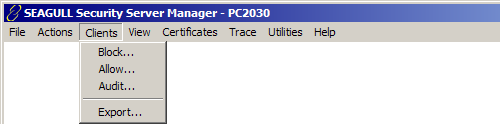

Displays the Block Clients dialog which allows the configuration of client IP address ranges or individual IP addresses to be blocked from connecting to the Security Server. Individual IP addresses within a blocked range may be allowed to connect using the Allow... function.
To configure an IP Address Range to block:
Enter the starting IP Address for the range in the From: edit box.
Enter the ending IP Address for the range in the To: edit box
Click the Add-> button to add the range to the blocked list.
Click the <-Remove button to remove a highlighted range from the list.
To configure Individual IP Addresses to block:
Enter an IP address in the Address: edit box.
Click the Add-> button to add the IP address to the blocked addresses list.
Click the <-Remove button to remove a highlighted address from the blocked addresses list.
Displays the Allow Clients dialog which allows the configuration of client IP address ranges or individual IP addresses in a blocked range to be allowed to connect.
Allow has precedence over Block. If an address is configured to be both blocked and allowed, it will be allowed.
To configure an IP Address Range to allow in a blocked range:
Enter the starting IP Address for the range in the From: edit box.
Enter the ending IP Address for the range in the To: edit box
Click the Add-> button to add the range to the allowed list.
Click the <-Remove button to remove a highlighted range from the list.
To configure Individual IP Addresses to allow in a blocked range:
Enter an IP address in the Address: edit box.
Click the Add-> button to add the IP address to the allowed addresses list.
Click the <-Remove button to remove a highlighted address from the allowed addresses list.
Displays the Audit Properties dialog. This feature, controls the writing of client connection information to the Windows Application Event Log. This information can be viewed using the NT/2000 Event Log Viewer. The NT/2000 Event Log Viewer can be launched from Security Server using View:Event Log.
Enable Client Auditing: Enables the recording of client connections and disconnections in audit logs.
Trace Failed Connections: If enabled, a trace of the SSL negotiation will be placed into the event log only if the negotiation fails. If the trace parameters specify Trace Full Data, the full data will be traced here as well. If it specifies Trace Summary Data, only the SSL status messages and number of bytes sent/received will be recorded, not the bytes themselves.
The Export feature is used to take a "snapshot" of the clients that are currently displayed in the Client List View panel.
 SEE
Tree
View:Clients for more information.
SEE
Tree
View:Clients for more information.
When Export is selected, you will be presented with a standard Windows file save dialog. Give the file a name and select the location where you want to store the file. Once the file is stored, you can view the contents of the file with Notepad.
Here is a sample of what the report will look like:
10.2.5.3-2788 iSeries
Secure 0:15:10
5734
302
10.2.5.6-3605 iSeries
Secure 0:00:50
552
50