Architecture and Design Considerations for Web Security
To understand the threats to web security and to help you prevent and counter these threats, you need to understand the processes and components that make up a web application, how the data flows through the application, and the trust boundaries.
Communication Stack for a Web Application
The following illustration shows the communication stack of a Uniface web application, including the components and processes that make up the application, and the data flow of an HTTP request and response. The dotted lines indicate the trust boundaries.
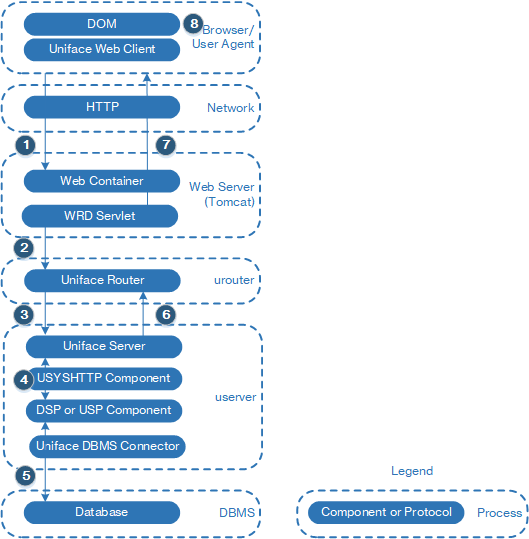
- The web browser (or other user agent, such as the UHTTP component) sends an HTTP request to web server (Tomcat) via the network.
- Tomcat starts a WRD servlet, which forwards
the request to the Uniface Router (
urouter). It uses information stored in the web.xml file, which contains aMIDDLEWAREparameter holding Uniface Router's server name and the port on which the Uniface Router is listening, as well as Uniface Router user name and corresponding password. - The Uniface Router checks the credentials and
forwards the request to the Uniface Server (
userver), adding information stored in the Router's assignment file (urouter.asn). - The Uniface Server calls the USYSHTTP component which parses the HTTP headers and activates the component specified in the HTTP request.
- The component may require data from the database, via the database connector.
- The Uniface Server then returns the request via Uniface Router to the WRD Servlet.
- The servlet returns the request to the HTTP client.
- If the client is a web browser, it renders and displays the result.
