Logical and Physical Connections
When a client application needs to connect to a Uniface Server, it does so via a Uniface Router, which makes the required physical connections from the client to the Uniface Server. The client may have multiple logical connections and each logical connection may pass over several physical connections.
For example, a client requires access to a shared
server (server1) and an exclusive server (server2). The logical
connections to these servers are specified in the client's assignment file:
[PATHS] $SRV1 = TCP:abc012345+13001|user|password|server1 $SRV2 = TLS:abc012345+13002|user|password|server2 /ex
The Uniface Router (urouter) has been started with two listening ports, one for TCP and the other for TLS:
urouter /asn=urouter.asn tcp:+13001 tls:+13002
The Uniface Router's assignment file contains the
following definitions for Uniface Servers server1 and
server2:
[SERVERS] server1 C:\uniface\common\bin\userver.exe /asn=userver.asn server2 C:\uniface\common\bin\userver.exe /asn=userver.asn
Connections to a Shared Server
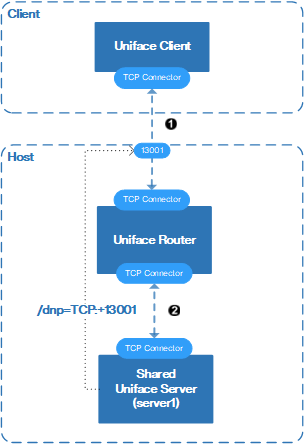
When the Uniface client wants a connection to the shared server, the connection is established as follows:
- The client connects to the Uniface Router
using the protocol, host, and port number specified by the
$SRV1path. In this case, the TCP protocol is specified.[PATHS] $SRV1 = TCP:abc012345+13001|user|password|server1
- The Uniface Router starts the requested server
(assuming it is not running yet), using the parameters specified by the UST definition for
server1:[SERVERS] server1 C:\uniface\common\bin\userver.exe /asn=userver.asn
By default, the Uniface Router requests the Uniface Server to use the first port in the list of listening ports that uses the same network connector as the client. In this case that is
TCP:+13001. So by default, the Uniface Router appends the /dnp qualifier to the servers command line:/dnp=TCP:+13001
- The requested server registers its availability with the Uniface Router, and opens a network channel to the Uniface Router to do so.
There are now two network connections:
- Between the client and the Uniface Router.
- Between the Uniface Router and the Uniface Server. This connection is used for all further communication between the Uniface Router and the Uniface Server.
Connections to an Exclusive Server
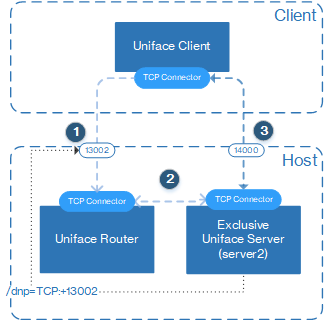
When a client uses an exclusive server, the Uniface Server can inherit the connection that the Uniface Router has to the client, but this is only possible for the TCP/IP protocol. For TLS (and optionally for TCP/IP when using the /gates qualifier), it creates its own listening port and gets the client to re-connect to that port. For example:
- When the Uniface client wants a connection to
the exclusive server, it connects to the Uniface Router using the protocol, host, and port number
specified by the
$SRV2path. In this case, the TLS protocol is specified.[PATHS] $SRV2 = TLS:abc012345+13002|user|password|server2 /ex
- The Uniface Router starts the requested server
(assuming it is not running yet), using the parameters specified by the UST definition for
server2:[SERVERS] server2 C:\uniface\common\bin\userver.exe /asn=userver.asn
It adds a /dnp switch to the command line so that the Uniface Server can register its availability with the Uniface Router, in this case
/dnp=tls:+13002. - A TLS exclusive server must listen to its own port. Because no /gates switch was used in the UST definition, it finds an unused port that it can use to listen on. Assume that this is 14000.
- The exclusive Uniface Server registers with
the Uniface Router using port
tls:+13002and informs the Uniface Router that it is listening on porttls:+14000. - The Uniface Router informs the client that it
must reconnect to
TLS:IP_Address+14000. (You can use the /hostrc switch to specify a host name instead of an IP address. For more information, see /hostrc.) - The Uniface Router and client, close their connection with each other
- The client now connects directly to the exclusive Uniface Server, instead of via the Uniface Router.
There is now only one network connection, but several connections were made in the process of establishing this connection:
- Temporary connection between the Uniface client to the Uniface Router. It is closed after the Uniface Router informs that client to reconnect using port TLS:+14000.
- Temporary connection between the Uniface Server and Uniface Router when the Uniface Server registers with the Uniface Router.
- Exclusive connection between the Uniface client and the Uniface Server.
Multiple Security Requirements
All of these connections may have different security requirements:
- Clients may be outside the firewall and the connection to the Uniface Router may need to be protected using the TLS connector.
- The Uniface Router and the Uniface Servers are normally on the same machine, behind the firewall, so their connections may require less security.
- For a client using an exclusive server, the initial connection to the Uniface Router and the eventual connection to the Uniface Server may need to be protected with TLS, but the temporary connection between the Uniface Router and Uniface Server may be different.
Applications have differing security needs and the TLS connector can be configured with varying levels of security. This can be done on a path by path basis so that an application can have multiple logical connections to servers, each using a different level of security. For more information, see TLS Connection Profiles.
Choosing Physical Connections
When deploying Uniface applications, you can choose which connection to use based on your security requirements.
For example, assume the Uniface Router has been
started with three listening ports, in which one port specifies a TLS connection profile called
most_secure:
urouter tcp:+13001 tls:+13002 tls:13003:most_secure
The client wants a connection to a shared server.
- The Uniface client connects to the Uniface
Router using the protocol, host, and port number specified by the
$SRV1path. In this case, the TLS protocol is specified.[PATHS] $SRV1=TLS:abc012345+13003:most_secure|user|password|server1
- The Uniface Router starts the requested server
(assuming it is not running yet), using the parameters specified by the UST definition for
server1:[SERVERS] server1 C:\uniface\common\bin\userver.exe /asn=userver.asn
By default, the Uniface Router requests the Uniface Server to use the first port in the list of listening ports that uses the same network connector as the client. In this case that is
TLS:+13002. So by default, the Uniface Router appends the /dnp qualifier to the servers command line:/dnp=TLS:+13002
Note: The Uniface Server is using a different TLS connection profile than the client — no connection profile is specified — so the parameters specified by the USYS$TLS_PARAMS setting will be used.
- If you want the same level of security as the
client connection, you can explicitly specify this using the /dnp qualifier in
the UST definition in Uniface Router assignment file:
[SERVERS] server1 C:\uniface\common\bin\userver.exe /asn=userver.asn /dnp=TLS:+13003:most_secure
- The Uniface Server now registers with the
Uniface Router on the listening port (13003) specified by the /dnp switch, and
uses the settings of the
most_secureTLS profile, if it has been defined in the [NET_SETTINGS] section of the assignment file.Alternatively, if you don't need the extra security between the Uniface Router and the Uniface Server, you could use
/dnp=tcp:13001. Because the network connector is different to the one used in the client/Uniface Router connection, you would also need to specify /altnet.
For more information, see TLS Connection Profiles, /dnp, and /altnet.
