Security tab
If you select the Use Group properties check box in the Account tab, then the configuration uses the group parameters and this tab is disabled. If you clear the check box, you can access
all of the configuration settings for this user. The options available on this page depend on the authentication type of
the group. For Windows Domain, RSA SecurID, and Novell iChain authentication types, all of the options except the User IP Address validation are disabled as the properties do not apply to those users. Only user ID/password authenticated users can access all the
options on this page.
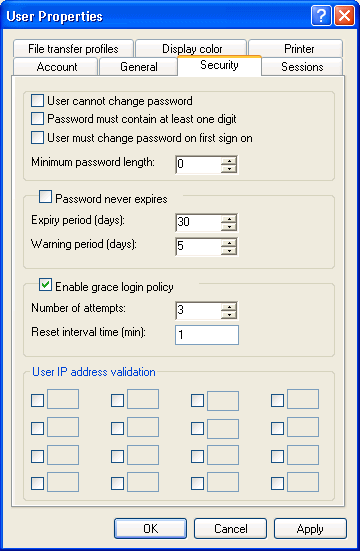
User cannot change password
Disables the Change password button on the client's ActiveX control toolbar preventing users from changing their passwords.
Password must contain at least one digit
Enhances password complexity.
User must change password at first sign on
Forces users to replace the passwords assigned to them by the administrator and define new passwords the first time they connect
to the cluster.
Minimum password length
Defines a minimum acceptable length policy for the user password. If the field is set to zero, a password of any length will
be acceptable, including an empty password.
Password never expires
Clear the check box to force users to change their passwords at regular intervals.
| • | Expiry period: Defines how often users must change their password. |
| • | Warning period: Defines the number of days before the end of the Expiry period that HAM sends the user a warning notification to change their password. The notification stops when the user changes the password. If the user does not change the password by the end of the expiry period, they cannot sign on until they change it. |
Enable grace login policy
Defines a policy to block users who attempt to sign on with the wrong password.
| • | Number of attempts: Defines the number of times the user can enter a wrong password before the account is locked. |
| • | Reset interval time: Defines the time (in minutes) after which the system automatically unlocks a locked account. |
User IP address validation
Defines IP address filters or access lists for the user. HAM allows you to define up to four subnets. The cluster accepts
connections only if the user's IP address belongs to the defined subnets. For example, if you define 10.1.1 and 10.1.2, then
the user can connect only if their IP address is in the ranges 10.1.1.0 to 10.1.1.255 and 10.1.2.0 to 10.1.2.255.