 SEE
How
to Configure the Clear Control Channel for more information.
SEE
How
to Configure the Clear Control Channel for more information.Connecting to the Host System
BlueZone Secure FTP supports the SSL protocol through the BlueZone Security Server or any other SSL enabled FTP connection including IBM Mainframe OS/390 and Z/OS, the iSeries OS/400 and other SSL enabled FTP servers. BlueZone Secure FTP may be pre-configured for distribution with the SSL feature enabled, eliminating the need for any end-user intervention in the installation or configuration process.
Security Options ----
To enable encryption, choose one of the following options:
None: Choosing "None" disables encryption.
Explicit FTPS (SSL/TLS): In this method, BlueZone Secure FTP connects to the typical FTP server port 21 and starts an unencrypted FTP session as normal, but requests that SSL/TLS security be used and performs the appropriate handshake before sending any sensitive data. This is the preferred method according to RFC 4217. Explicit FTPS is also sometimes referred to as AUTH TLS.
Implicit FTPS (SSL/TLS): In this method, BlueZone Secure FTP connects to a non-typical port (usually 990), and an SSL/TLS handshake is performed before any FTP commands are sent.
Enable Clear Control Channel: - If enabled, BlueZone Secure FTP will attempt to use a clear control connection but an encrypted data connection.
 SEE
How
to Configure the Clear Control Channel for more information.
SEE
How
to Configure the Clear Control Channel for more information.
Enable Clear Data Channel: - If enabled, BlueZone Secure FTP will send the data in the Data Channel without any encryption.
SFTP (SSH): Enables Secure FTP known as SSH. When you are connected to an SFTP host, a small padlock will be displayed on the StatusBar as shown here.
If you click the padlock with your left mouse button, an SFTP Connection Status dialog will be displayed, as shown here:
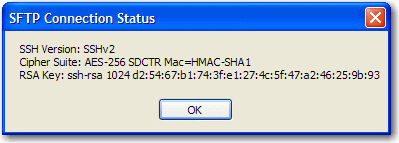
Encryption Type ----
Specifies which version of the SSL protocol should be used. The following options only apply to Explicit FTPS and Implicit FTPS. You must specify one or the other.
SSL v3: (Default)- Specifies that SSL version 3 should be used.
TLS v1: Specifies that TLS version 1 should be used.
 NOTE SSL
v3 and TLS v1 are nearly
identical. TLS
v1 is preferred.
NOTE SSL
v3 and TLS v1 are nearly
identical. TLS
v1 is preferred.
Invalid Certificates ----
Specifies how to handle an invalid server certificate. Options include:
Always Reject: Specifies that an invalid server certificate should always be rejected.
Ask Before Accepting: Specifies that the user should be asked whether to accept an invalid server certificate.
Always Accept: Specifies that an invalid server certificate should always be accepted.
Preferred Cipher Suite: If you have a preference, choose a Cipher Suite from the "drop down" box. Otherwise leave it set to AES.
 NOTE This
product includes software developed by the OpenSSL Project for use in
the OpenSSL Toolkit. (http://www.openssl.org/)
NOTE This
product includes software developed by the OpenSSL Project for use in
the OpenSSL Toolkit. (http://www.openssl.org/)
Related Topics: